Blogs

ASD’s ACSC, CISA, FBI, NSA, and International Partners Release Best Practices for Event Logging and Threat Detection
Protecting Your Organization from Living Off the Land (LOTL) Cyberattacks
Are You Ready? CMMC Update
CISA and FBI Release Update to Advisory – Royal Ransomware Actors Rebrand as “BlackSuit,”: August 7, 2024
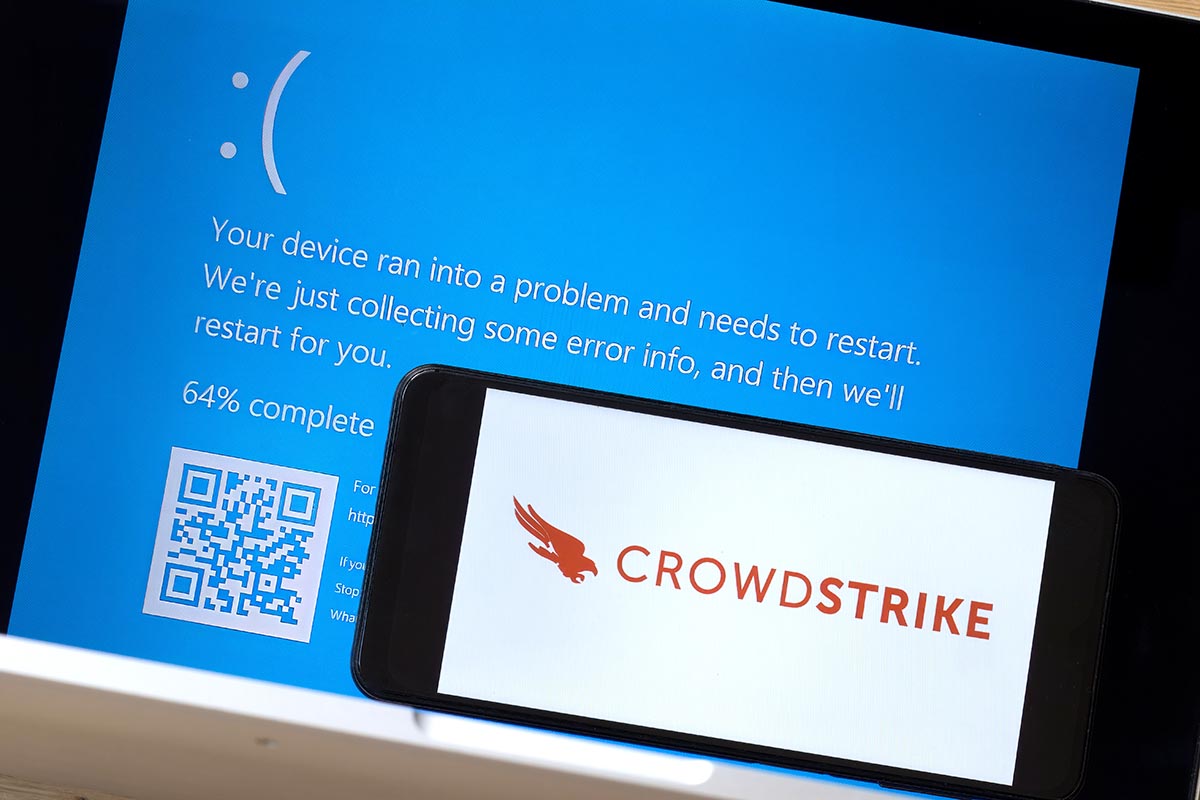
How the CrowdStrike Outage Impacted Small Businesses Across the Globe: July 25, 2024
CISA, FBI, and Partners Release Advisory Regarding North Korean Cyber Espionage Activity: July 25, 2024
More Information Unfolds on the Microsoft/CrowdStrike Global IT Disruption: July 22, 2024
CISA Alerts: July 12, 2024 – AT&T Discloses Breach of Customer Data
CISA Alerts: July 8, 2024 – CISA & ASD’s ACSC Release Joint Advisory on PRC APT40 Tradecraft in Action
Categories
- AI
- CISA Alerts
- Cloud Computing
- Cloud Infrastructure
- CMMC
- Compliance
- Critical Infrastructure
- Cybersecurity
- Cybersecurity Advisories
- Department of Defense
- Firmware
- Government
- IT Consulting
- IT Managed Services
- Managed IT
- Managed Service Provider
- Managed Services
- News
- Ransomware
- Recruiting
- Social Media
- Staffing
- Technology
- Uncategorized
- Vulnerability Management
Tags
ABB MV Drives AI Anti-Malware Anti-virus CISA CISA Alerts CMMC compliance Compliance as a service coronavirus covid19 critical infrastructure CSA cyberattacks cybersecurity Cyber Security Cybersecurity Advisories Cybersecurity Advisory cybersecurity threat detection cyber threats data breaches Desktop Support endpoint protection FBI firmware firmware attacks Firmware Compromise healthcare incident response plans Industrial Control Systems Information Technology IT consulting IT managed services Malicious Firmware malware Managed IT Services Managed Service Provider Managed Services managed services provider microsoft Microsoft Windows MSP multi-factor authentication Network Security NSA phishing ransomware recruiting Schneider Electric Siemens small and medium-sized businesses SMBs Software spam Spry Squared virus Vulnerability Vulnerability Management Vulnerability Management. critical infrastructure Windows 10